Preemptive cybersecurity defense refers to the ability to detect and disrupt fraud and account takeover attempts before credentials are misused and damage occurs. According to a 2026 analyst brief from Frost & Sullivan, most enterprise fraud and cybersecurity controls still activate too late in the attack lifecycle to prevent loss. As a result, organizations are absorbing financial, regulatory, and reputational impact even when traditional defenses are technically “working.”
That conclusion marks a turning point. Fraud is no longer escalating because attackers are inventing new techniques. It is escalating because defenses engage after the exposure window has already opened.
Why fraud prevention keeps failing on timing
The Frost & Sullivan report is explicit about the root cause behind rising fraud losses: timing, not sophistication.
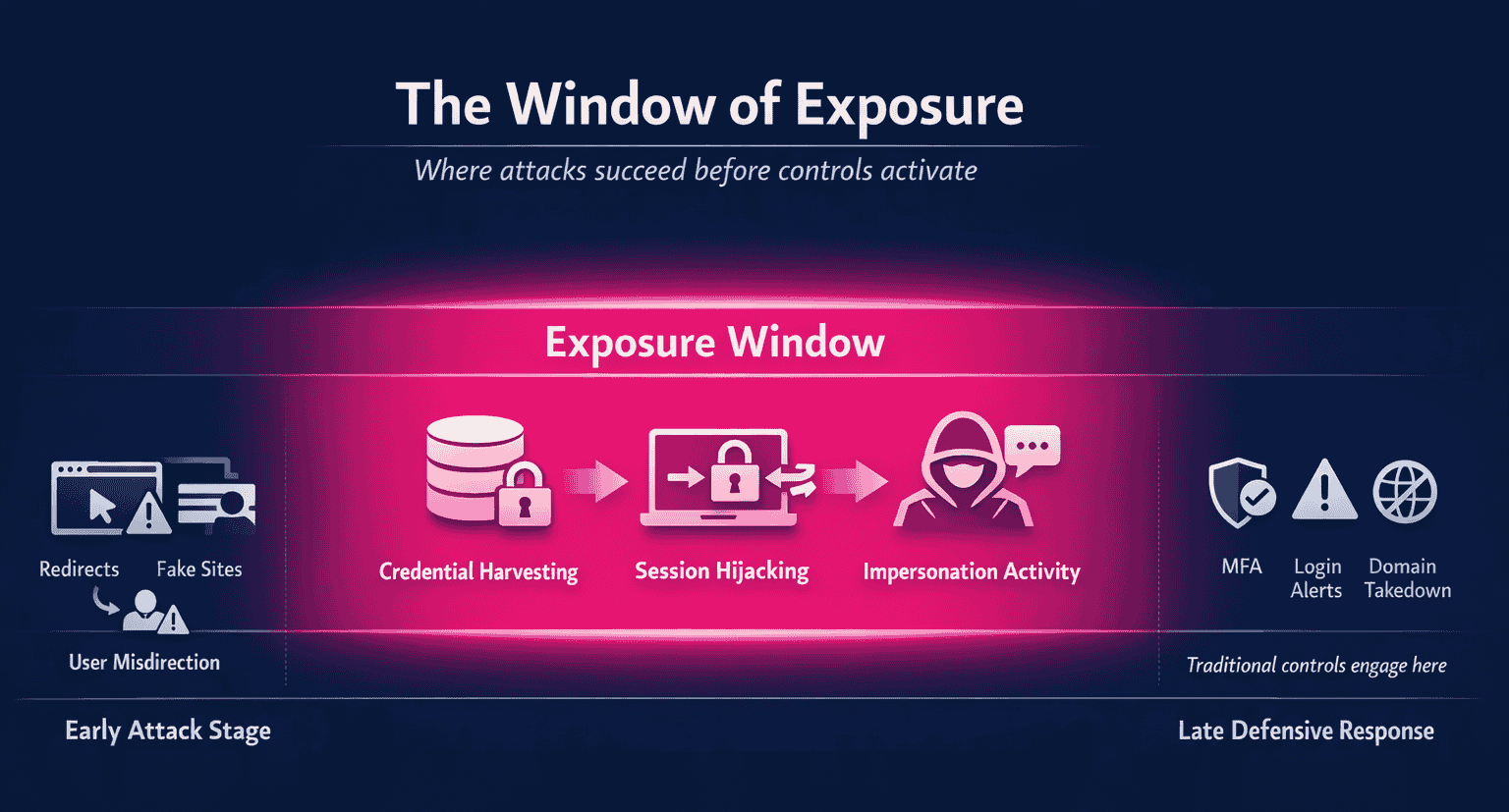
Modern digital impersonation attacks, phishing campaigns, and credential harvesting operations unfold rapidly and upstream. Victims are redirected to fake sites, misled by cloned assets, or guided through fraudulent flows long before a legitimate login attempt ever occurs. By the time most controls activate, the attack has already progressed past the point where prevention is possible.
This is especially true as attackers increasingly rely on AI-assisted automation to scale scams. Automation allows fraud campaigns to compress reconnaissance, impersonation, and credential theft into a narrow window that legacy defenses are structurally unable to see. The mechanics have not changed. The speed and scale have.
Why most “real-time” fraud controls activate after exposure
Many fraud and cybersecurity solutions advertise real-time detection. In practice, Frost & Sullivan finds that most of these controls still engage post-exposure, during or after authentication.
This includes:
-
Fraudulent site takedowns that occur after credentials are harvested
-
Multifactor authentication that can be bypassed through adversary-in-the-middle techniques
-
Suspicious login verification that activates only once stolen credentials are replayed
These approaches share a common limitation. They respond after the attacker has already interacted with the victim. Credentials, once harvested, continue to circulate and be reused long after a fake site has been taken down. Victims often remain unidentified. SOC and fraud teams are left reconstructing incidents instead of preventing them.
The result is a widening exposure window where fraud succeeds quietly, without triggering alerts in time to stop it.
How regulation is forcing earlier fraud intervention
Frost & Sullivan also connects timing failures directly to regulatory pressure. Reimbursement and shared-responsibility frameworks increasingly assume that organizations have earlier visibility into scam-driven activity, not just post-incident evidence.
Examples cited in the report include:
-
UK APP fraud reimbursement rules
-
The EU Instant Payments Regulation and Verification of Payee
-
Singapore’s Shared Responsibility Framework
-
Nacha ACH fraud rules in the United States
Across regions, the pattern is consistent. Regulators are shifting accountability upstream, implicitly penalizing late detection. Organizations that discover fraud only after funds move or accounts are taken over face growing reimbursement obligations and compliance exposure.
Fraud prevention timing is no longer a technical preference. It is becoming a balance-sheet risk.
What Frost & Sullivan defines as the missing capabilities in modern fraud defense
Frost & Sullivan’s analysis points to a clear conclusion: enterprises require a new class of fraud defense capabilities that operate before authentication, use deception to disrupt attackers, and provide real-time visibility into affected users and devices.
Preemptive cybersecurity defense focuses on identifying and disrupting impersonation-led fraud during the exposure window, before credentials are exploited or monetized. It emphasizes early-stage detection, deception, and lifecycle disruption rather than post-attack response.
This approach is designed to:
-
Surface impersonation and credential harvesting attempts as they emerge
-
Identify affected users and malicious devices in real time
-
Disrupt attacker workflows before fraud escalates
In short, it extends protection into the stages of the attack lifecycle where prevention is still possible.
Why Frost & Sullivan highlights Memcyco in this context
Frost & Sullivan highlights Memcyco’s solution as an example of how these preemptive capabilities can be implemented in practice, particularly where early impersonation detection, deception, and victim-level visibility are required.
Rather than relying solely on takedowns or post-authentication signals, Memcyco is cited for its ability to intervene during impersonation-driven exposure, enabling earlier identification of targeted users and disruption of attacks before credentials are misused. The analyst brief emphasizes outcomes such as real-time visibility into individual victims, attack lifecycle disruption, and the use of deception to neutralize harvested data.
Importantly, the endorsement is not about a single feature. It reflects alignment with the broader architectural shift Frost & Sullivan describes, one that prioritizes earlier engagement over faster reaction.
What this endorsement signals to enterprise security leaders
The Frost & Sullivan report makes one point clear: this is not a tooling debate. It is an architectural one.
As fraud becomes more automated and impersonation-driven, security programs that depend on late-stage controls will continue to absorb losses they never had a chance to prevent. Preemptive defense is emerging as a foundational layer, closing the visibility gap that attackers exploit between first contact and credential misuse.
For enterprise leaders, Frost & Sullivan’s analysis provides independent validation that earlier intervention is no longer optional. The organizations that adapt will reduce fraud exposure and regulatory risk. Those that do not will continue responding after the damage is already done.
Book a product tour and discover the preemptive cybersecurity defenses endorsed by Frost & Sullivan. During your demo we’ll tailor the narrative to explain how Memcyco performs in your specific scenarios.
Related Reading
-
Why Fast Company Named Memcyco a 2025 ‘Next Big Thing in Tech’ for Cybersecurity
-
MFA Isn’t Enough: How Attackers Bypass Authentication and What Actually Stops Account Takeovers
-
How to Detect and Stop Reverse Proxy Phishing Attacks in Real-Time
Frequently Asked Questions
What is preemptive cybersecurity defense?
Preemptive cybersecurity defense is a model that detects and disrupts fraud and impersonation attempts before credentials are misused. It focuses on early-stage signals during exposure rather than post-attack response.
Why do traditional fraud prevention tools fail against impersonation attacks?
Most tools activate after authentication or after credentials are stolen. By then, attackers have already interacted with victims, and prevention opportunities have passed.
How does timing affect fraud and account takeover prevention?
Timing determines whether controls engage before or after exposure. Late-stage detection allows credential harvesting and account takeover to succeed even if alerts eventually fire.
Why are regulators pushing for earlier fraud detection?
Reimbursement and shared-responsibility frameworks increasingly assume earlier visibility into scam-driven activity. Late detection exposes organizations to financial and compliance risk.
How does Frost & Sullivan evaluate modern fraud defense models?
Frost & Sullivan emphasizes preemptive detection, deception-based defense, and lifecycle disruption as critical capabilities for addressing modern, automated fraud.